PKI Tutorials - Herong's Tutorial Examples - v2.32, by Herong Yang
HTTPS Server Authentication Process
This section describes the HTTPS server authentication process - 1. CA root certificate installed in the browser; 2. Web server certificate signed by the CA; 3. Web server certificate validated by the browser.
As mentioned in the previous section, Web server authentication is an important process to ensure the security of the HTTPS communication. The following diagram from washburnsworld.blogspot.com shows how Web server authentication is done at a high level:
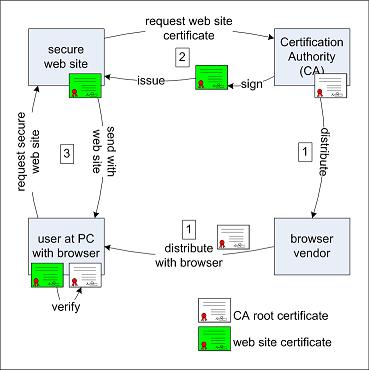
As you can see from the diagram, there are 3 major activities involved in Web server authentication process:
1. Installing CA (Certificate Authority) root certificate - The browser vendor receives the CA root certificate from the CA; and distributes it as part of the browser installation package.
2. Signing Web server certificate - The Web server owner sends the certificate request to the CA. The CA, acting as the RA (Registration Authority), verifies the Web server identity. Then the CA signs (or issues) the Web server's certificate.
3. Validating Web server certificate - When you use the browser to visit the Web server, the browser, acting as the VA (Validation Authority), receives the Web server's certificate and validates it against the CA root certificate. If the browser finds no issue in the server certificate, it starts to use the public key embedded in the server certificate to secure the communication with the server.
The goal of HTTPS Web server authentication is to help the browser, on behave of you (the Web server user), to build a trust with the Web server before exchanging data with the server. If the browser returns an error when validating the server certificate, you know that the server can not be trusted and you should stop using that Web server.
But if the browser returns no error when validating the server certificate, can you really trust the server? Yes, you can trust the Web server, if following assumptions are true:
- You trust the browser vendor properly installed the CA root certificate in the browser.
- You trust the CA properly verified the Web server's identity.
- You trust the browser properly validated the Web server's certificate.
Table of Contents
Introduction of PKI (Public Key Infrastructure)
►Introduction of HTTPS (Hypertext Transfer Protocol Secure)
What Is HTTPS (Hypertext Transfer Protocol Secure)?
►HTTPS Server Authentication Process
HTTPS Communication Data Encryption
Using HTTPS with Google Chrome
Using HTTPS with Mozilla Firefox
HTTPS with IE (Internet Explorer)
Android and Server Certificate
Windows Certificate Stores and Console
RDP (Remote Desktop Protocol) and Server Certificate
macOS Certificate Stores and Keychain Access
Perl Scripts Communicating with HTTPS Servers
PHP Scripts Communicating with HTTPS Servers
Java Programs Communicating with HTTPS Servers
.NET Programs Communicating with HTTPS Servers
CAcert.org - Root CA Offering Free Certificates
PKI CA Administration - Issuing Certificates
Comodo Free Personal Certificate
Digital Signature - Microsoft Word
Digital Signature - OpenOffice.org 3